Class 4: LOCAL AREA NETWORK
A Local Area Network (LAN) is a computer network that operates within a limited geographic area, such as a home, office, school, or corporate campus. LANs are designed to facilitate high-speed communication and resource sharing among connected devices. The boundaries of a LAN are typically confined to a single building or a group of buildings within a defined campus
Steps to Build a simple Wired LAN
- Verify Ethernet Connectivity – Ensure that all computers have functional Ethernet Network Interface Cards (NICs) to support wired connections. Otherwise add NIC card.
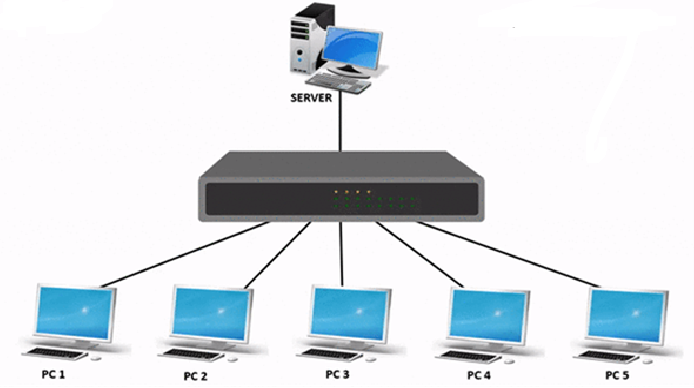
- Determine Network Size and Select Networking Equipment – If the network consists of more than two devices, use a network switch (preferred) or a hub to interconnect them.
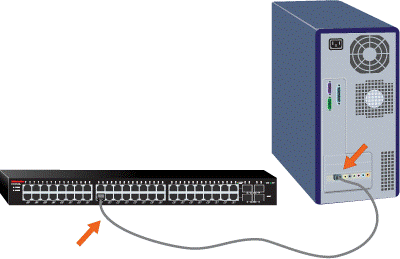
- Establish Physical Connections – Connect each computer’s Ethernet port to the switch or hub using Ethernet cables (Cat5e/Cat6), cable ends will be RJ45.
- Verify Operating System Availability – Ensure that all computers have a functional network support operating system (either the same or different) .
- Confirm Protocol Configuration – Install and configure a common protocol suite, typically TCP/IP, to enable seamless communication among devices.
- Assign IP Addresses – Configure each computer with a unique IP address within the same logical network (subnet). Avoid IP address duplication to prevent conflicts. (network part should be same and host part should be different)
- Test Network Connectivity – Use the ping command to verify connectivity between devices and ensure proper network communication.

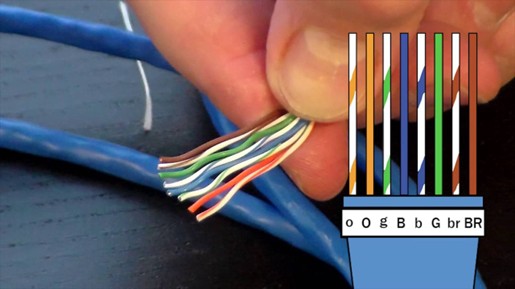
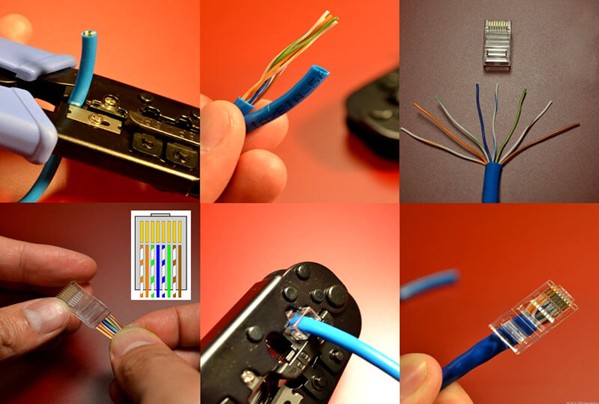
How to Crimp an RJ45 Connector for LAN Cables
Tools and Materials Required:
- Crimping Tool – Used to attach RJ45 connectors to the cable.
- RJ45 Connectors – Modular plugs that connect Ethernet cables to networking devices.
- Ethernet Cable (Cat5e, Cat6, or Cat7) – The twisted-pair cable used for networking.
- Cable Stripper – To remove the outer sheath of the cable.
- Cable Tester – To verify the connection is correctly wired and functioning.
- Scissors or Wire Cutter – For trimming the wires.
Step-by-Step Crimping Process:
Step 1: Prepare the Ethernet Cable
- Use a cable stripper to remove about 1-2 inches of the outer sheath from the Ethernet cable.
- Untwist the pairs of wires carefully to avoid damage.
- Arrange the wires according to the required wiring standard (T568A or T568B).
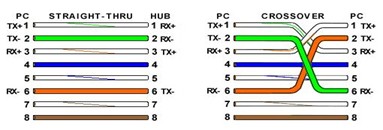
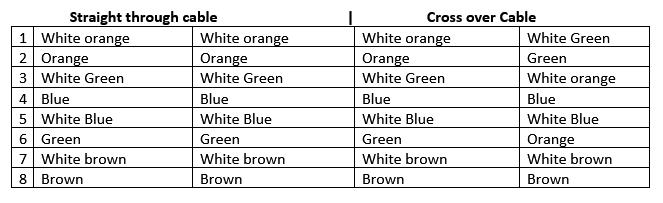
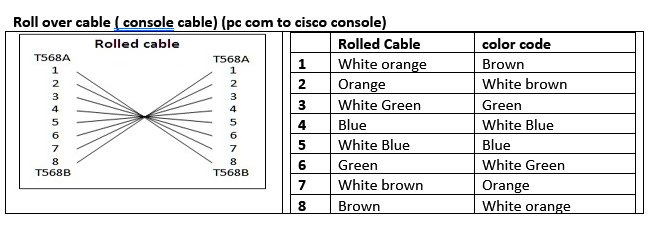
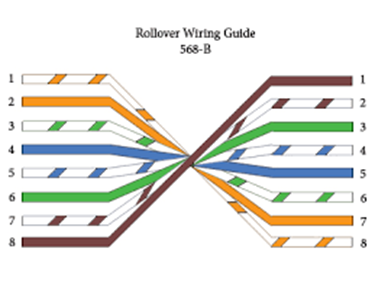
- T568A: White-Green, Green, White-Orange, Blue, White-Blue, Orange, White-Brown, Brown.
- T568B (Most Common): White-Orange, Orange, White-Green, Blue, White-Blue, Green, White-Brown, Brown.
Step 2: Trim and Align the Wires
- Ensure the wires are straightened and aligned correctly.
- Use a wire cutter to trim the wires to an even length (about 0.5 inches from the sheath).
Step 3: Insert the Wires into the RJ45 Connector
- Holding the RJ45 connector with the clip facing down, carefully insert the wires into the connector, ensuring each wire reaches the end.
- Double-check the wire order before proceeding.
Step 4: Crimp the Connector
- Place the RJ45 connector into the crimping tool’s designated slot.
- Firmly squeeze the crimping tool handles to press the pins down onto the wires.
- Release the tool and gently pull on the cable to ensure a secure connection.
Step 5: Test the Cable
- Plug both ends of the cable into a cable tester.
- Turn on the tester and check if all pairs light up correctly.
- If any wires are misaligned or disconnected, redo the crimping process.
Tips for Successful Crimping:
- Always double-check the wiring order before inserting wires into the RJ45 connector.
- Avoid stripping too much of the outer sheath to prevent loose connections.
- Use a high-quality crimping tool to ensure a secure fit.
- If a mistake is made, cut off the connector and redo the process to maintain a reliable network connection.



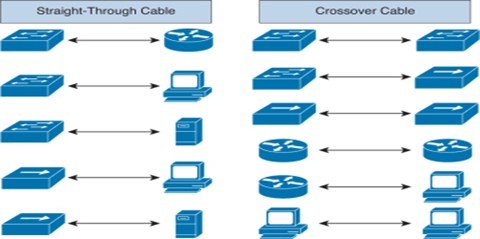
A structured cabling system
A structured cabling system consists of various components that ensure a reliable, scalable, and organized network infrastructure. Below are the key equipment and components required for structured cabling:
Passive Network Components (Non-Powered Devices)
Network Cables – The primary medium for data transmission.
- Twisted Pair Cables (Cat5e, Cat6, Cat6a, Cat7, Cat8) – Used for Ethernet networking.
- Fiber Optic Cables (Single-mode & Multi-mode) – Used for high-speed and long-distance communication.
- Coaxial Cables – Used in legacy networks and cable TV systems.
Patch Panels – Used for terminating and organizing cables coming from different locations.
- Helps in easy troubleshooting, expansion, and cable management.
Faceplates & IO (Information Outlet) Boxes – Wall-mounted boxes where network cables terminate.
- Usually installed at user desks for Ethernet connections.
Keystone Jacks (RJ45 Jacks) – Modular connectors fitted into patch panels, faceplates, and IO boxes.
- Used to terminate Ethernet cables securely.
Cable Trays & Conduits – Used to route and protect network cables within the building.
RJ45 Connectors – Connectors used for Ethernet cable terminations.
Cable Ties & Velcro Straps – Used for organizing and managing cables neatly.
Cable Labels & Tags – Essential for documenting and identifying cable connections.
Grounding & Bonding Equipment – Ensures protection from electrical surges.
Active Network Components (Powered Devices)
Network Switches – Devices that connect multiple computers and network devices.
- Unmanaged Switches – Simple plug-and-play switches with no configuration.
- Managed Switches – Allows VLANs, QoS, security policies, and monitoring.
Routers – Connects different networks and manages data traffic between them.
- Used for WAN connectivity and Internet access.
Modems & Gateways – Used to convert ISP signals (fiber, DSL, or cable) into Ethernet signals.
Firewalls – Ensures network security by filtering traffic and blocking unauthorized access.
PoE (Power over Ethernet) Switches or Injectors – Supplies power and data to devices like IP phones, security cameras, and access points over a single cable.
Wireless Access Points (APs) – Extends network coverage for Wi-Fi users.
Network Racks & Cabinets – Houses networking equipment like switches, patch panels, and power units for organized management.
Uninterruptible Power Supply (UPS) – Provides backup power to prevent downtime in case of power failures.
Testing & Monitoring Tools
Cable Tester – Verifies continuity and connectivity of cables.
Fluke Network Tester – Advanced tool for signal strength, speed, and interference testing.
LAN Analyzer / Network Monitoring Software – Helps in real-time network performance monitoring.


Basic LAN testing and troubleshooting Commands
1. IP Configuration Commands
- Windows: ipconfig
- Displays the current network configuration settings for all interfaces.
- Additional parameter: ipconfig /all
- Shows detailed information including DNS servers, MAC address, and DHCP status.
- Linux: ifconfig
- Displays configuration information of network interfaces.
- Note: In many Linux distributions, ifconfigis being replaced by ip.
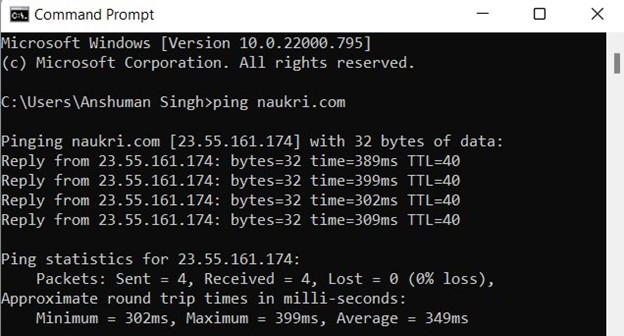
2. Ping Command
- Purpose:Tests the reachability of a host on a network by sending Internet Control Message Protocol (ICMP) Echo Request messages.
- Self Ping:ping 127.0.0.1
- Tests the local loopback interface to verify if TCP/IP is properly configured.
- Interface Card Ping:ping 192.168.1.10
- Pings another device on the local network.
- Gateway Ping:ping 192.168.1.1
- Tests the connectivity to the default gateway.
- Internet Ping:ping 8.8.8.8
- Tests connectivity to an external IP address, in this case, Google’s public DNS.
- Other Devices:Ping other devices within the network by using their respective IP addresses.
- Self Ping:ping 127.0.0.1
3. Traceroute Command
- Command:tracert 8.8.8.8 (Windows) / traceroute 8.8.8.8 (Linux)
- Traces the route packets take to reach an external IP address, providing insights into the network path and identifying potential bottlenecks.
4. Network Statistics Command
- Command:netstat
- Displays active connections, routing tables, and various network statistics, which can be essential for troubleshooting connectivity issues.
5. DNS Cache Command
- Command:ipconfig /displaydns (Windows)
- Displays the contents of the DNS resolver cache, providing information on recently resolved domain names.
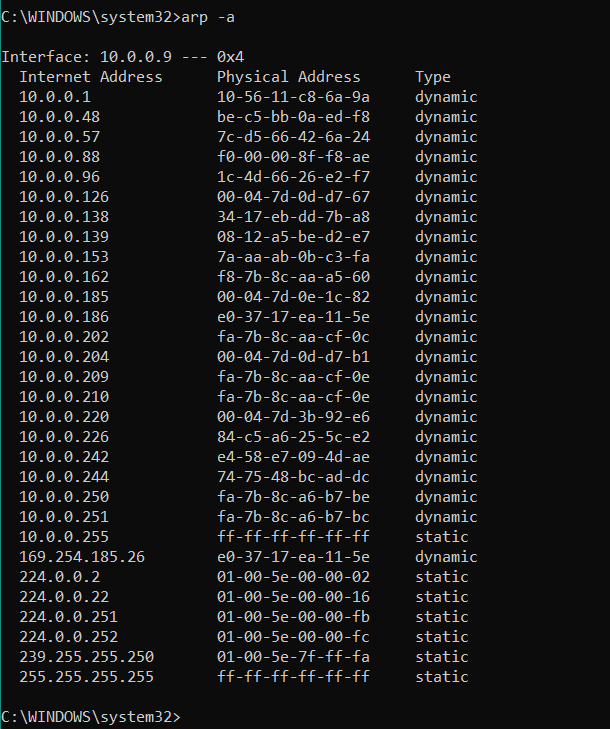
6. ARP Command
- Command:arp -a
- Displays the ARP cache, which maps IP addresses to MAC addresses on the local network. This can help verify if the devices are reachable on the local segment.
short note on IP Address, MAC Address, and ARP
IP Address: A unique logical address assigned to devices for communication in a network. Works at Layer 3 (Network Layer). Example: 192.168.1.1 (IPv4).
MAC Address: A unique physical address assigned to a device’s network interface card (NIC). Works at Layer 2 (Data Link Layer). Example: 00:1A:2B:3C:4D:5E.
ARP (Address Resolution Protocol): A protocol that maps an IP address to a MAC address within a local network. Command: arp -a to view ARP table.
IP = Logical Address | MAC = Physical Address | ARP = IP to MAC Mapping
How ARP (Address Resolution Protocol) Works
Purpose: ARP resolves an IP address to a MAC address for communication within a local network.
Step-by-Step ARP Process:
- Device Needs MAC Address → A sender wants to communicate with an IP (e.g., 192.168.1.10) but doesn’t know its MAC address.
- ARP Request (Broadcast) → The sender sends a broadcast message:
- “Who has IP 192.168.1.10? Tell me your MAC address.”
- Switch/Hub send this broadcast message to all the ports other than received port
- ARP Reply (Unicast) → Only The target device (192.168.1.10) responds with its MAC address.
- Cache Update → The sender stores this MAC in its ARP cache for future use.
Communication Begins → Now, data can be sent using the resolved MAC address.
What is Ping
The full form of PING is the Packet InterNet Groper. It is a computer network management system software or utility software used to test the network communication between two devices.
What is Web server
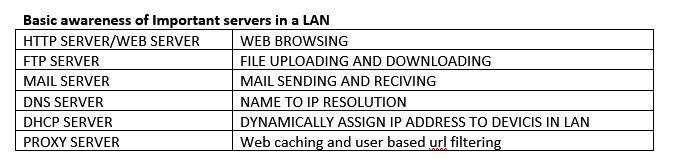
A web server is a software application that runs on a computer and is responsible for hosting, managing, and serving websites, web applications, and other web-based content over the internet.
Here’s how it works:
- Client Request: A user types a URL or clicks a link, sending a request to the web server.
- Server Processing: The web server receives the request, processes it, and retrieves the requested data (e.g., HTML files, images, videos).
- Server Response: The web server sends the requested data back to the client (user’s web browser) in the form of HTTP responses.
- Client Rendering: The client’s web browser receives the data, renders the webpage, and displays it to the user.

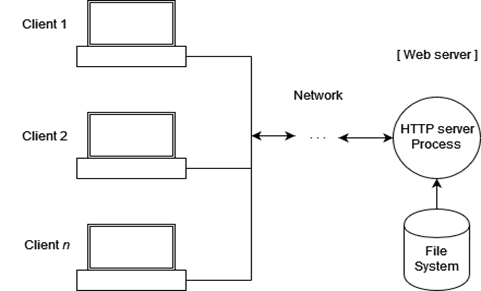
Examples of Web Servers
- Apache HTTP Server – One of the most widely used web servers, developed in 1996 and maintained by the Apache Software Foundation. It is open-source, cross-platform, and supports Linux, Windows, macOS, and more.
- Microsoft IIS (Internet Information Services) – A proprietary web server developed by Microsoft, integrated with Windows Server. It provides a graphical interface for configuration and supports ASP.NET, PHP, and other technologies.
- Apache Tomcat – A specialized Java-based web server and servlet container initially developed by Sun Microsystems and later maintained by the Apache Software Foundation. It supports Java applications along with PHP, ASP.NET, Perl, and Python.
- Lighttpd – A lightweight and efficient web server, known for its low memory, CPU, and disk usage. Developed in 2003, it is commonly used in embedded systems such as routers, webcams, and other small hardware devices.
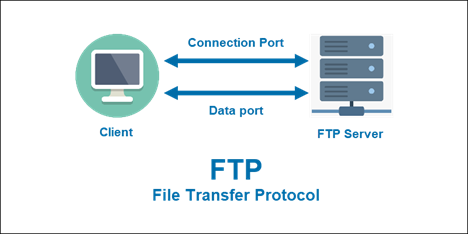
FTP SERVER – File Transfer Protocol
FTP Server
An FTP server is a software application that enables users to transfer files between computers over a network using the File Transfer Protocol (FTP).
Key Features
– Enables file transfers between computers
– Supports various FTP clients and protocols (e.g., FTP, SFTP, FTPS)
– Provides user authentication and access control
– Often used for website maintenance, file sharing, and data exchange

Examples: JSCAPE, Progress MOVEit, FileZilla, Cerberus Server, Globalscape, Titan Server, IIS FTPS Server, Core FTP, Sysax Multi Server
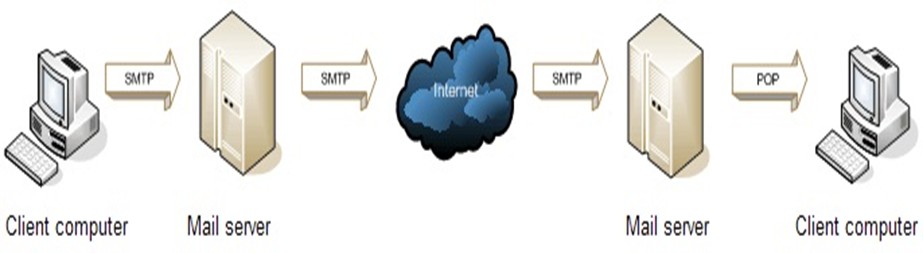
Mail Server
What is a Mail Server?
A mail server is a software and hardware system that handles and delivers emails over a network, typically using the SMTP, IMAP, and POP3 protocols. It acts as a digital post office, storing, sending, receiving, and managing emails between users.
How It Works:
- A user sends an email using an email client (e.g., Outlook, Gmail).
- The SMTP server processes and forwards the email to the recipient’s mail server.
- The recipient’s IMAP or POP3 server stores the email, allowing the user to retrieve it.
Types of Mail Servers:
- Outgoing Mail Server (SMTP Server): Sends emails to other mail servers.
- Incoming Mail Server (IMAP/POP3 Server): Stores and delivers emails to recipients.
SMTP POP/IMAP examples:
agorum core, Apache James, Axigen, Citadel, CommuniGate Pro, Courier
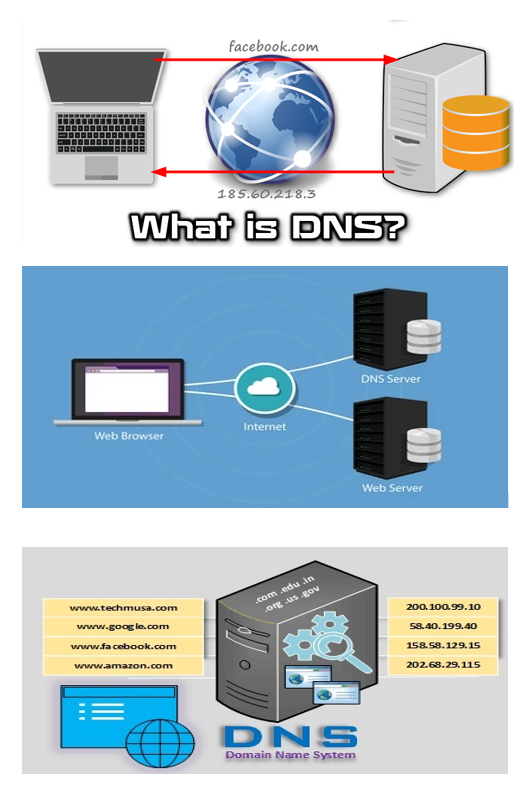
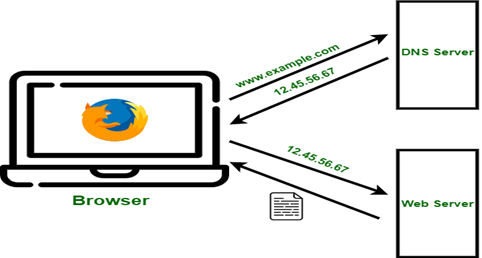
What is a DNS Server?
A DNS (Domain Name System) server is a system that translates domain names (e.g., www.google.com) into IP addresses (e.g., 172.217.160.238), allowing computers to locate and communicate with each other over the internet.
How It Works:
- When a user enters a website URL in a browser, a request is sent to a DNS server.
- The DNS server checks its database to find the corresponding IP address for the domain name.
- The browser uses this IP address to connect to the website’s web server and loads the page.
Examples of DNS Server Software
- BIND (Berkeley Internet Name Domain) – The most widely used open-source DNS server, commonly found in Unix and Linux environments.
- Cisco Network Registrar (CNR) – A commercial DNS server by Cisco Systems, often used alongside CNR DHCP servers for handling high volumes of dynamic DNS updates.
- Dnsmasq – A lightweight DNS forwarder, ideal for small-scale networks, providing local DNS resolution and caching.
- djbdns – A security-focused DNS server designed by Daniel J. Bernstein, known for its efficiency and reliability.
- Microsoft DNS – The built-in Windows DNS server, integrated with Active Directory, supporting authoritative, recursive, and hybrid modes, making it the default choice for many enterprise networks.
- Posadis – A C++-based DNS server, offering Dynamic DNS update support and flexibility for smaller networks.
- PowerDNS – A versatile DNS server supporting multiple storage backends and load balancing, with separate implementations for authoritative and recursive DNS functions.
DHCP SERVER
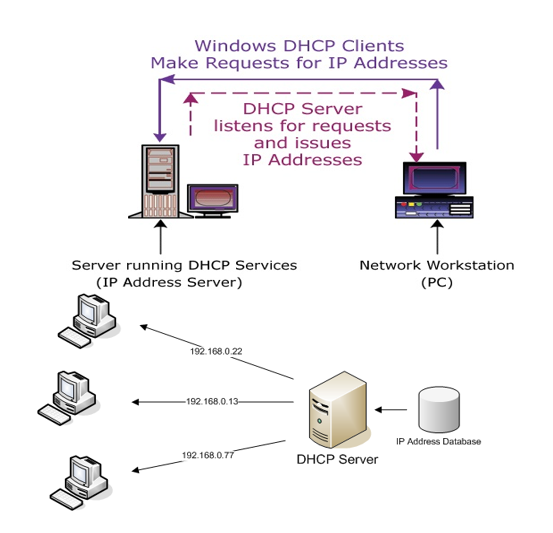
What is a DHCP Server?
A DHCP (Dynamic Host Configuration Protocol) server is a network service that automatically assigns IP addresses and other network configurations to devices (clients) in a network. This eliminates the need for manual IP configuration and ensures efficient IP address management.
How It Works:
- A device (client) connects to a network and sends a DHCP request.
- The DHCP server assigns an available IP address, subnet mask, gateway, and DNS settings.
- The client leases the assigned IP for a specific time, after which it must renew or release it.
Examples of DHCP Servers
- dhcpy6d – A DHCPv6 server designed for managing IPv6 address assignments in enterprise networks.
- Dibbler – A cross-platform DHCPv6 server and client, supporting dynamic IPv6 address allocation.
- Dnsmasq – A lightweight DHCP and DNS caching server, ideal for small-scale networks and embedded systems.
- ISC DHCP – A widely used, open-source DHCP server developed by the Internet Systems Consortium (ISC), supporting both IPv4 and IPv6.
- FreeRADIUS – Primarily an authentication and authorization server, but also includes DHCP capabilities for network access control.
- Jagornet DHCP – A high-performance DHCPv6 server, designed for large-scale IPv6 deployments.
- Kea DHCP – A modern DHCP server from ISC, designed for scalability and high performance, supporting both IPv4 and IPv6.
- Udhcpd – A lightweight DHCP server designed for embedded systems and small networks.
- WIDE-DHCPv6 – A specialized DHCPv6 server used for IPv6 address allocation in research and enterprise environments.
- Microsoft DHCP Server (Windows Server)
- Cisco IOS DHCP Server (Routers & Switches)
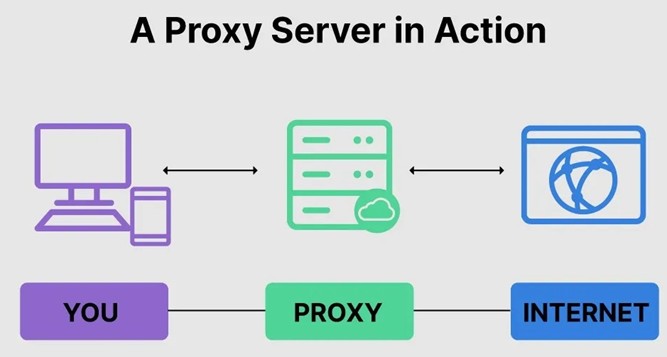
What is a Proxy Server?
A proxy server is an intermediary server that sits between a client (user device) and the internet, handling requests on behalf of the client. It acts as a gateway, forwarding requests to web servers and returning the responses to the user.
The word proxy means “to act on behalf of another,” and a proxy server acts on behalf of the user. All requests to the Internet go to the proxy server first, which evaluates the request and forwards it to the Internet. Likewise, responses come back to the proxy server and then to the user.
How a Proxy Server Works:
- The user sends a request (e.g., opening a website).
- The proxy server processes and forwards the request to the destination server.
- The web server responds to the proxy, which then delivers the data to the user.
Key Functions of a Proxy Server:
- Security & Privacy – Hides the user’s IP address, enhancing anonymity and protecting against cyber threats.
- Content Filtering – Blocks access to specific websites based on policies (e.g., workplace or school restrictions).
- Performance Improvement – Caches frequently accessed content to reduce bandwidth usage and speed up access.
- Access Control – Restricts or allows users to access specific content based on permissions.
- Bypassing Geo-Restrictions – Enables users to access region-restricted content by routing traffic through different locations.
Types of Proxy Servers:
- Forward Proxy – Used by clients to access the internet indirectly.
- Reverse Proxy – Sits in front of web servers to balance loads and provide security.
- Transparent Proxy – Intercepts and forwards traffic without modifying it or hiding the user’s IP.
- Anonymous Proxy – Masks the user’s identity for privacy.
A proxy server is commonly used in corporate networks, educational institutions, cybersecurity setups, and content delivery networks to enhance security, control access, and optimize performance.
Examples of Proxy Servers
- Squid Proxy – A popular open-source caching and forwarding proxy for web acceleration and content filtering.
- Apache HTTP Proxy – A proxy module for Apache HTTP Server, used for load balancing and caching.
- Nginx Reverse Proxy – Commonly used as a reverse proxy to improve performance and security.
- HAProxy – A high-performance TCP/HTTP load balancer and reverse proxy, widely used in enterprise environments.
- CCProxy – A user-friendly Windows-based proxy server, often used for internet sharing and filtering.
- Privoxy – A proxy server focused on privacy enhancements, ad-blocking, and content filtering.
- WinGate – A full-featured proxy server, VPN, and firewall solution for businesses.
- Blue Coat ProxySG – A commercial enterprise-grade proxy server offering advanced security and content filtering.
- Tor (The Onion Router) – Functions as an anonymous proxy, routing traffic through multiple encrypted nodes for privacy.
- TinyProxy – A lightweight HTTP proxy designed for low-resource environments.
Basic LAN Troubleshooting
1.Physical Connectivity Issues
Ensure Ethernet cables are properly connected.
Check power and status lights on network devices.
Use a cable tester to identify faulty connections.
2.IP Configuration Issues
Verify IP settings using `ipconfig` (Windows) or `ifconfig` (Linux).
Ensure correct subnet mask & gateway configuration.
Check DHCP server settings if using dynamic IPs.
3.Slow Network Performance
Identify high bandwidth usage with monitoring tools.
Reduce unnecessary network broadcasts.
Upgrade to Gigabit Ethernet for better speed.
4.VLAN & Routing Issues — details covered later
Use `show vlan brief` to check VLAN configurations.
Verify routing settings & default gateway.
Check for Spanning Tree Protocol (STP) loops.
5.DNS Issues — details covered later
Use `nslookup` or `dig` to check DNS resolution.
Try changing to Google DNS (8.8.8.8) or Cloudflare (1.1.1.1).
6.Duplicate IP Addresses — details covered later
Use `arp -a` to detect conflicts.
Assign unique static IPs or configure DHCP properly.
7.Firewall & Security Blocks – – details covered later
Check firewall rules and disable temporarily for testing.
Ensure correct port forwarding & ACL settings.
8.Wi-Fi (WLAN) Issues – details covered later
Move closer to the router for better signal.
Change Wi-Fi channel to reduce interference.
Use WPA2/WPA3 security for safe connectivity.
Basic Troubleshooting Commands
`ping <IP>` – Test connectivity.
`tracert <IP>` – Check network path issues.
`netstat -an` – View active network connections.
`arp -a` – Detect duplicate IPs.
`show interfaces` – Check switch/router interface status.
Class 3
Basics of networking
Jump to Class 1
Introduction to Cisco